CyberArk is the global leader in privileged access security, a critical layer of IT security to protect data, infrastructure, and assets across the enterprise, in the cloud and throughout the DevOps pipeline.
CyberArk delivers the industry’s most complete solution to reduce the risk created by privileged credentials and secrets. The company is trusted by the world’s leading organizations, including more than 50 percent of the Fortune 500, to protect against external attackers and malicious insiders. CyberArk is named a Leader in the 2018 Gartner Magic Quadrant for Privileged Access Management – positioned both highest in execution and furthest in vision.
CyberArk pioneered the market and remains the leader in securing enterprises against cyber attacks that take cover behind insider privileges to attack critical enterprise assets. Today, only CyberArk delivers a new category of targeted security solutions that help leaders stop reacting to cyber threats and get ahead of them, preventing attack escalation before irreparable business harm is done.
With offices and authorized partners worldwide, CyberArk is a vital security partner to more than 4,800 global businesses.
THE CYBERARK SOLUTION
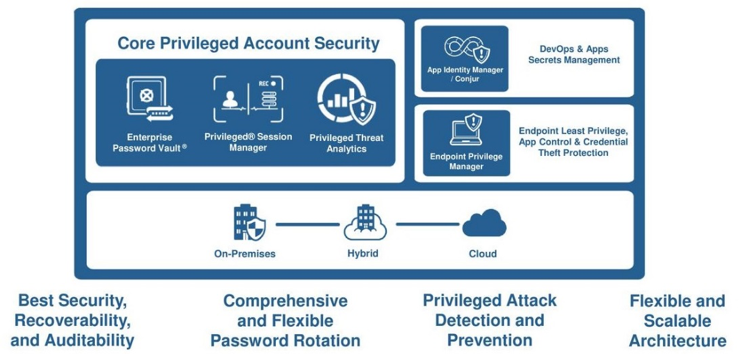
The CyberArk Privileged Access Security Solution is the industry’s most complete solution for protecting, controlling, and monitoring privileged access across on-premises, cloud, and hybrid infrastructure. Designed from the ground up for security, the CyberArk solution helps organizations efficiently manage privileged account credentials and access rights, proactively monitor and control privileged account activity, intelligently identify suspicious activity, and quickly respond to threats.
CORE PRIVILEGED ACCOUNT SECURITY
- Credential protection and management.
The CyberArk solution centrally secures and controls access to privileged credentials based on privileged access security policies. Automated password and SSH key rotation reduce the time-consuming and error-prone task of manually tracking and updating privileged credentials to easily meet audit and compliance standards.
- Isolate, control, monitor, and record privileged sessions.
The CyberArk solution isolates and secures privileged user sessions, protects target systems from malware on endpoints, and enables privileged account access without exposing sensitive credentials. The solution supports broad connection methods with native access for cloud administrators and privileged business users, Windows clients (e.g. RDP, SSMS, etc.) and native command-line SSH device connectivity. Monitoring and recording capabilities enable security teams to view privileged sessions in real-time, automatically suspend and remotely terminate suspicious sessions, and maintain a comprehensive, searchable audit trail of privileged user activity.
- Analytics and alerting on malicious privileged access activity.
Threat detection and analytics enable organizations to detect, alert, and respond to anomalous privileged activity indicating an in-progress attack. The solution collects a targeted set of data from multiple sources and applies a complex combination of statistical and deterministic algorithms. This allows organizations to detect indications of compromise early in the attack lifecycle by identifying malicious privileged access activity.
The solution uses machine learning algorithms to examine typical patterns of individual privileged users, privileged accounts, and system activities to determine a baseline of “normal behavior.” It compares real-time activity to the baseline to identify unusual user behavior and system activity indicative of an attack including suspected credential theft, lateral movement, and privilege escalation.
APPLICATION PROTECTION
Application Access Manager helps organizations control, manage and audit non-human privileged access for a wide range of applications across on-premises, hybrid and cloud environments. Protecting credentials for application and other non-human identities is critical for organizations. Non-human credentials are ubiquitous. Unfortunately, hard-coded credentials are too often embedded in many different types of applications, including commercial off-the-shelf-solutions, internally-developed business-critical applications and within the CI/CD toolchain of DevOps.
Part of the CyberArk Privileged Access Security Solution, Application Access Manager provides privileged access and credential and secrets management for a wide variety of application types, including:
- Commercial off-the-shelf solutions: Provides and manages credentials for third-party tools and solutions including security and IT operation tools, RPA (Robot Process Automation) and other automation, as well as configuration management and orchestration tools.
- Internally-developed traditional applications: Protects business-system data and simplifies operations by eliminating hard-coded credentials from applications and scripts developed internally by the organization.
- Cloud-native applications built using DevOps methodologies: Meets the dynamic needs of DevOps and cloud-native environments to manage secrets and credentials used by non-human entities – including CI/CD toolchains, containerized applications, and PaaS environments.
ENDPOINT PROTECTION
CyberArk Endpoint Privilege Manager helps remove the barriers to enforcing least privilege and allows organizations to block and contain attacks at the endpoint, reducing the risk of information being stolen or encrypted and held for ransom. A combination of privilege management, application control, and targeted credential theft protection stops and contains damaging attacks at the endpoint of entry. Unknown applications run in a restricted mode to contain threats and credential theft protection blocks credential theft attempts. These critical protection technologies are deployed as a single agent to strengthen and harden all desktops, laptops, and servers.
CyberArk Endpoint Privilege Manager also enables security teams to enforce granular least privilege policies for IT administrators, helping organizations effectively segregate duties on Windows servers. Complementing these privilege controls, the solution also delivers application controls designed to manage and control which applications are permitted to run on endpoints and servers.
PARTNERSHIP
IS4U is an official partner from CyberArk since 2013 and has the Certified Partner level.
To be able to achieve this partnership level it is required that IS4U has proven and certified competences in all fields including sales, technical pre-sales and implementation of the CyberArk security solutions:
- CyberArk Certified Sales Professionals (CSP)
- CyberArk Certified Pre-Sales Engineers (CPE)
- CyberArk Certified Delivery Engineers (CDE)
At IS4U we continuously keep investing in CyberArk trainings and certifications for our security professionals, not only for our partnership with CyberArk but also as confirmation of our experience in privileged account security and our proven expertise in the field.


